Firewall¶
The Firewall menu item allows you to set the parameters for the router’s firewall. Various settings are possible here.
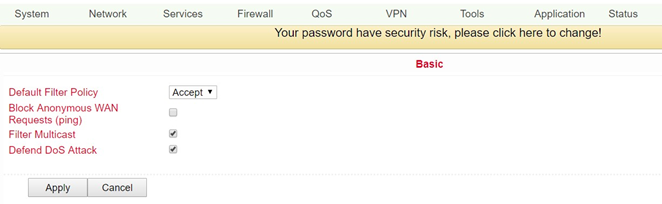
Basic¶
Here you can configure the basic settings of the firewall.
Name |
Description |
Default |
|---|---|---|
Default Filter Policy |
Possible options are allow and block |
Allow |
Block Anonymous WAN Request (ping) |
Enable to block ping requests generated anonymously from the network |
Disabled |
Filter Multicast |
Click to enable filtering of multicast |
Enabled |
Defend DoS Attack |
Click to enable fending off DoS attacks |
Enabled |
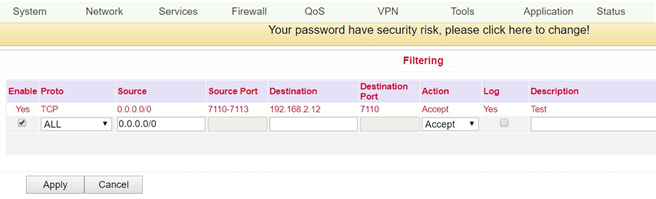
Filtering¶
At this point you can filter what the firewall should let through and what not. Various configurations are possible here, which you can reach via Firewall > Filtering.
Name |
Description |
Default |
|---|---|---|
Enable |
Click to activate filtering |
Enabled |
Proto |
Selection of the protocol. The options “TCP”/”UDP”/”ICMP” are possible |
All |
Source |
Set source IP address |
Blank |
Source Port |
Set source port if corresponding protocol was selected |
Blank |
Destination |
Set destination IP |
Blank |
Destination Port |
Set destination port if corresponding protocol was selected |
Blank |
Action |
Selection whether setting should be accepted or blocked |
Allowed |
Log |
Click to enable logging of the setting |
Disabled |
Description |
Describe configuration |
Blank |
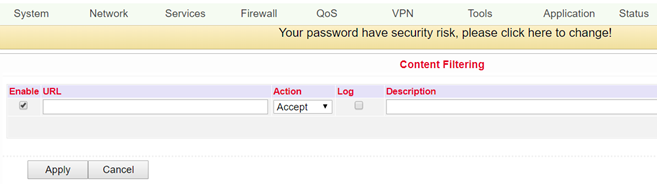
Content Filtering¶
The content filter in the firewall allows you to filter the call of special URLs, which can then be blocked or allowed. You can create the configuration under Firewall > Content Filtering.
Name |
Description |
Default |
|---|---|---|
Enable |
Enable or disable the content filter function |
Enabled |
URL |
Entering the URL to be blocked or filtered |
Blank |
Action |
Selection whether URL is blocked or accepted |
Enabled |
Log |
Can be activated for logging |
Disabled |
Description |
Describe configuration |
Blank |
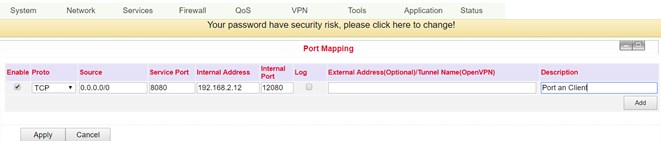
Port Mapping¶
NAT-PMP (NAT Port Mapping) allows a computer in a private network (behind a NAT router) to automatically configure the router so that devices behind the router can be reached from outside the private network. It essentially controls what is known as port forwarding. NAT-PMP, like UPnP also, and allows a program to request all incoming data from outside on a specific TCP or UDP port. You can perform the configuration under**Firewall > Port Mapping**.
Name |
Description |
Default |
|---|---|---|
Enable |
Enable or disable port mapping |
Enabled |
Proto |
Selection of TCP, UDP or TCP&UDP protocols |
TCP |
Source |
Enter source IP |
0.0.0.0/0 |
Service Port |
Enter port of the service |
8080 |
Internal Address |
Set internal IP for mapping |
Blank |
Internal Port |
Set port mapping to “internal” |
8080 |
Log |
Click to enable logging of port mapping |
Disabled |
External Address (Optional) / Tunnel Name (OpenVPN) |
Used in conjunction with VPN. For port forwarding with VPN, the virtual VPN IP address of the TC router must be entered here |
Blank |
Description |
Describe the meaning of the individual classifications |
Blank |
Virtual IP Mapping¶
The IP of an internal PC can be assigned to a virtual IP. An external network can access the internal PC via this virtual IP address. You can set up this configuration under Firewall > Virtual IP Mapping.
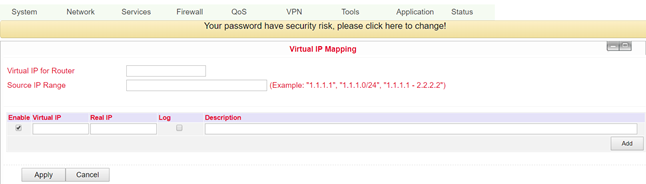
Name |
Description |
Default |
|---|---|---|
Virtual IP for Router |
Set virtual IP for router |
Blank |
Source IP Range |
Set range of source IP addresses |
Blank |
Virtual IP |
Set virtual IP |
Blank |
Real IP |
Set real IP |
Blank |
Log |
Enable logging for virtual IP |
Disabled |
Description |
Describe configuration |
Blank |
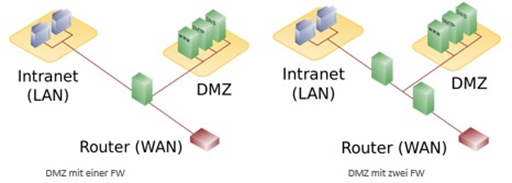
DMZ¶
A Demilitarized Zone (DMZ) refers to a computer network with security-controlled access to the servers connected to it.
The systems set up in the DMZ are shielded from other networks (e.g. Internet, LAN) by one or more firewalls. This separation allows access to publicly accessible services while protecting the internal network (LAN) from unauthorized access from the outside.
The purpose is to make services of the computer network available to both the Internet (WAN) and the intranet (LAN) on as secure a basis as possible.
A DMZ provides protection by isolating a system from two or more networks.
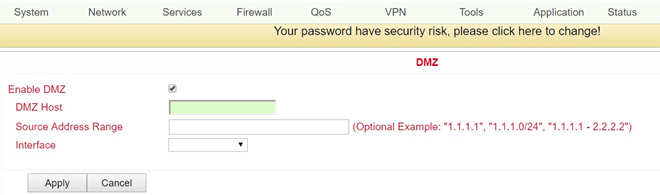
By mapping all ports and the external PC, you can access all ports of the device connected to the TK500.
With this function it is not possible to assign the administration port of the TK500 (e.g.: 80 TCP) to the port of the device. To forward port 80, change the management port of the router under System > Admin Access.
Name |
Description |
Default |
|---|---|---|
Enable DMZ |
Click to enable DMZ |
Disabled |
DMZ Host |
Set DMZ host IP |
Blank |
Source Address Range |
Set IP address with restricted IP access |
Blank |
Interface |
Selection of the appropriate interface |
Blank |
MAC-IP Bundling¶
MAC IP bundling means assigning a predefined IP address to a defined MAC address. Thus the given MAC address always gets the same IP address. You can reach this menu item under Firewall > MAC-IP Bundling.
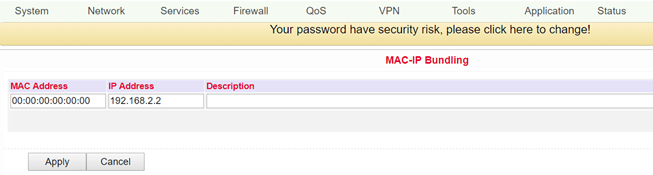
If a firewall blocks all access to the external network, only PCs with MAC-IP bundling will gain access to the external network.
Name |
Description |
Default |
|---|---|---|
MAC Address |
Set MAC address for bundling |
Blank |
IP Address |
Set IP address for bundling |
192.168.2.2 |
Description |
Describe configuration |
Blank |
NAT¶
Network Address Translation (NAT) In computer networks, Network Address Translation is the collective term for procedures that automatically replace address information in data packets with other information in order to connect different networks. They are therefore typically used on routers.
Use of Source-NAT (SNAT)¶
It allows devices with private network addresses to connect to the Internet. Private IP addresses cannot usually be routed by the provider, so they must be translated into a public, routable IP address. The TK500v2 has implemented this function, which enables communication between different networks. In addition, a relevant security aspect is found in NAT, since a public IP address cannot be traced back to the associated private IP address.
Use of Destination-NAT (DNAT)¶
This is used to offer services that are operated on computers under a single IP address. It is often referred to as port mapping or port forwarding.
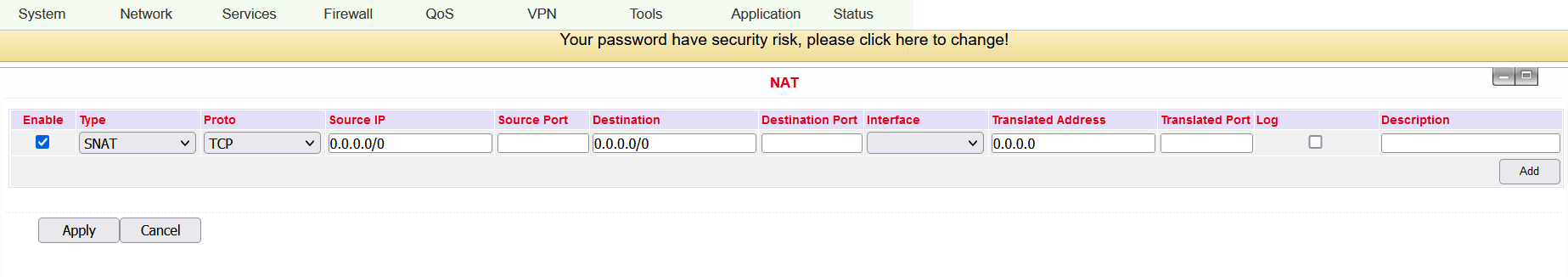
Configuration¶
To configure NAT, go to the menu item Firewall and select the subitem NAT.
Here you can find a list of all existing NAT rules
New NAT rules can be added via the Add button